In this article Janua’s CTO share tips and tricks about Keycloak X509 Certificate Authentication.
1. Overview
The goal is to explain how it is possible to authenticate user against keycloak applications using client certificates.
This can be very useful in case of direct access grant, where the user want to authenticate against keycloak using REST API.
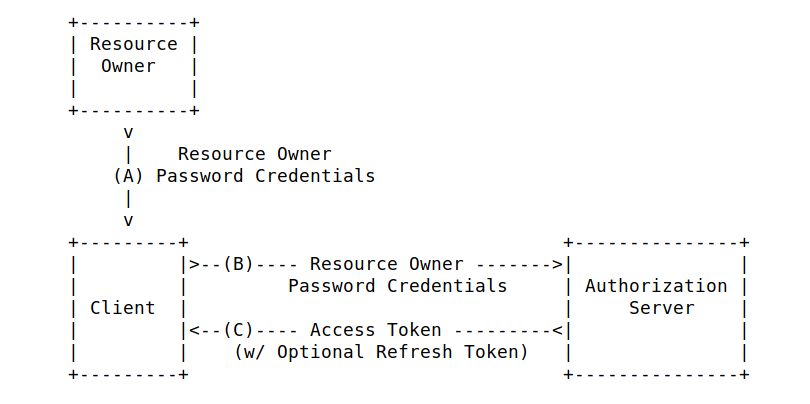
Direct Access Grant is the only oauth2/openid flow which allows to perform REST API calls. But, unfortunately, this flow is not secured, as the user credentials are exposed as it is on the wire.
| POST /token HTTP/1.1 Host: server.example.com Authorization: Basic czZCaGRSa3F0MzpnWDFmQmF0M2JW Content-Type: application/x-www-form-urlencoded grant_type=password&username=johndoe&password=A3ddj3w |
2. Drawback of direct access grant Oauth2 code flow
As can be seen above, the direct access grant flow, expose directly the user credentials on the wire (username/password) making such an invocation quite vulnerable to MITM attacks (man in the middle attacks)
This type of flow is a major security breach.
3. Keycloak using X509 certificate
It is possible with keycloak to define a new authentication flow similar to direct access, called X509 direct access,based on certificates.
This authentication flow is very secure, as there is no password transiting on the wire.
Like this, it is possible to authenticate a user against keycloak using directly the user certificate.
Example:
| curl –insecure https://localhost:8593/auth/realms/master/protocol/openid-connect/token \ -H ‘Authorization: Basic YXBwLWpzcDpmN2M3MjUyNC0yYzZjLTRiMTEtOGRiNS1hNWQ0ZTBlN2Q1Zjg=’ -H ‘content-type: application/x-www-form-urlencoded’ \ -d ‘grant_type=password’ -E /home/orivat/dev/keycloak/x509_auth/openssl_tests/user1.crt \ –key /home/orivat/dev/keycloak/x509_auth/openssl_tests/user1.key Enter PEM pass phrase: {« access_token »: »eyJhbGciOiJSUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICJmMjladkc0eXBxMWo2RENnYzk0QzZKMDIwZTdYX1J5MExxMTNoejdCdTAwIn0.eyJqdGkiOiI1YjA0Yzg1Ni1hM2U1LTQ4MmUtOTRhYy1lNTc5OGY4NDVkNjQiLCJleHAiOjE1NjM4OTE0NT …… ……… MsIm5iZiI6MCwiaWF0IjoxNTYzODkxMzkzLCJpc3MiOiJodHRwczovL2xvY2FsaG9zdDoLCJzY29wZSI6InByb2ZpbGUgZW1haWwifQ.xzOu6GUpLTMWDOXEntNoaecL2PNNEkqbbiU8DVRTGlE », »token_type »: »bearer », »not-before-policy »:1563886376, »session_state »: »4625130d-5018-484e-bb88-75c7a982e164″, »scope »: »profile email »} |
4. Deployement
For any possible deployement of this specific X509 authentication flow customization , don’t hesitate to contact us.
- New Keycloak online training - 19 janvier 2022
- Sizing Keycloak or Redhat SSO projects - 8 juin 2021
- Keycloak.X Distribution - 28 janvier 2021