One of the cool features in the upcoming release of OpenIDM is the new Admin UI.
Source : https://marginnotes2.wordpress.com/2014/11/17/openidm-trying-the-new-admin-ui/
Thanks Marc CRAIG’s blog.
If like me you have been out of the loop for a while, it is reassuring to see that OpenIDM still installs a dream when you are just getting started. Download, unzip, and ./startup.sh.
Here is how you might start OpenIDM with an existing sample. This uses sample2, which is one-way synchronization with OpenDJ. You are not required to start with the samples, but they can quickly bootstrap your evaluation, without requiring you to read much doc or to think through the initial configuration.
$ cd /path/to && mv ~/Downloads/openidm . && cd openidm $ ./startup.sh -p samples/sample2 Executing ./startup.sh... Using OPENIDM_HOME: /path/to/openidm Using PROJECT_HOME: /path/to/openidm/samples/sample2 Using OPENIDM_OPTS: -Xmx1024m -Xms1024m Using LOGGING_CONFIG: -Djava.util.logging.config.file=/path/to/openidm/samples/sample2/conf/logging.properties Using boot properties at /path/to/openidm/samples/sample2/conf/boot/boot.properties OpenIDM version "3.1.0-RC3-SNAPSHOT" (revision: 4297) jenkins-OpenIDM-3746 null -> OpenIDM ready
OpenIDM’s web based UI is ready for HTTPS out of the box, but it seems you can still use HTTP for evaluation.
For example, you can visit https://localhost:8080/openidmui/ and login as openidm-admin:openidm-admin.
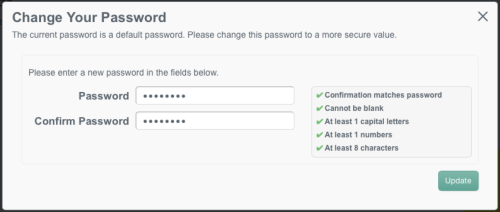
OpenIDM’s UI helps prevent default passwords by prompting you to change your password the first time you login.
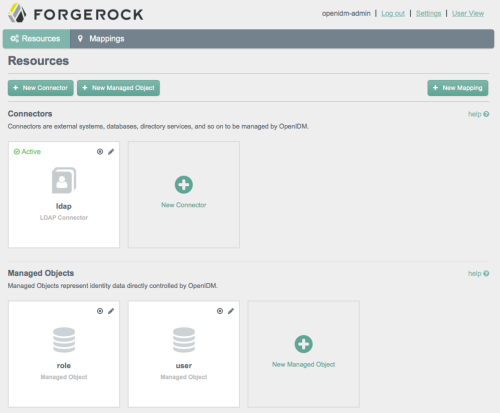
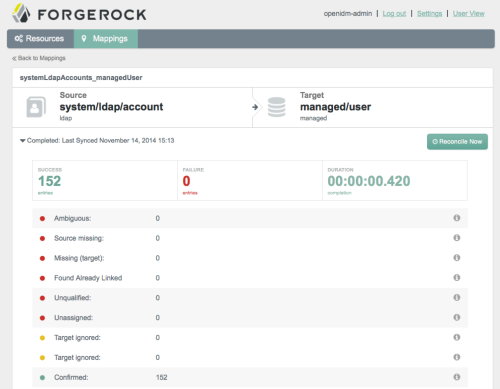
You find the Admin UI at https://localhost:8080/admin/. This shows the view when running with the sample2 configuration.
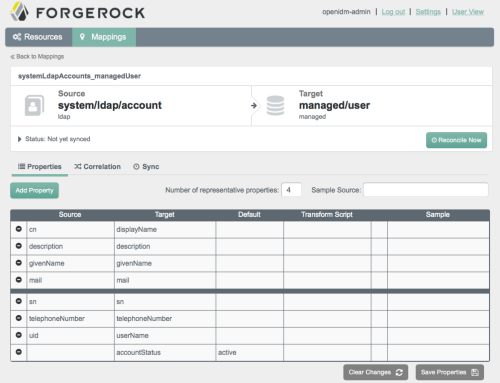
The new Admin UI offers a wizard-like approach to setting up provisioning. If you follow sample2, set up OpenDJ with some sample data before you get started. The sample comes with a mapping from OpenDJ accounts to managed/user.
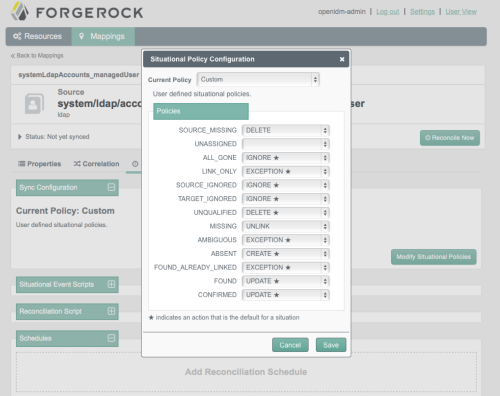
The sample also comes with a configuration for what to do in different situations during synchronization. Most of the policies are defaults.
To run reconciliation and synchronize your source and target, either click the Reconcile Now or schedule reconciliation on the Sync Tab of the Mappings page. When reconciliation completes, you should have a bunch of new managed users. If you schedule reconciliation, subsequent runs might not encounter any changes.
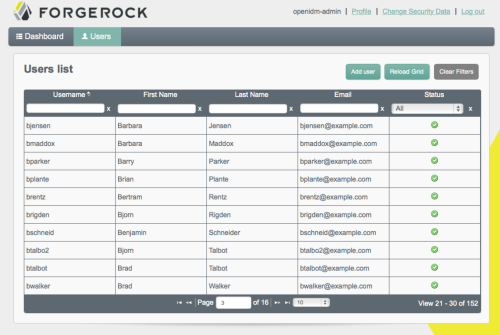
Click the User View link at the upper left of the page and then the Users tab to view all your managed users.
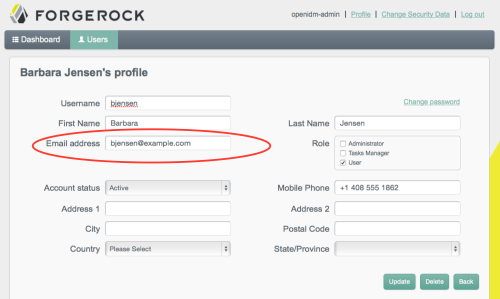
When you change a mapped attribute in the source, in this case OpenDJ, reconciliation updates it in the target, in this case the managed/user. For example, Babs Jensen’s original mail address is bjensen@example.com.
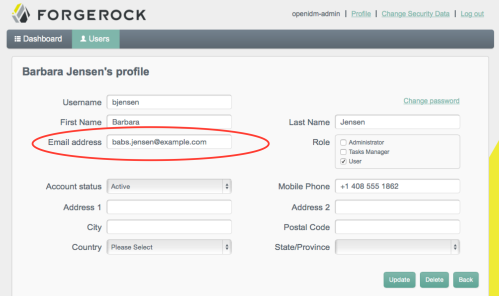
After changing the mail address in OpenDJ to babs.jensen@example.com, reconciliation updates her corresponding managed/user in OpenIDM’s repo. Refreshing the page after reconciliation, you can see the change.
The OpenIDM Admin UI is quite a leap forward, and promises to make it much easier for all of us to create and edit resources and mappings, and to arrange and schedule synchronization. Hats off to the OpenIDM team!
- New Keycloak online training - 19 janvier 2022
- Sizing Keycloak or Redhat SSO projects - 8 juin 2021
- Keycloak.X Distribution - 28 janvier 2021