In this article are exposed some of the key concepts protecting a Keycloak RedHat SSO with a reverse proxy in production.
Protecting the keycloak server is crucial. Keycloak server should not be visible from the outside
1) Why adding a reverse proxy
The goal of the reverse proxy is to hide/mask off keycloak authentication server from the external (i.e the internet). It allow to protect efficiently a keycloak server deployment.
As a result, the end-user will only have access to the reverse proxy URL, and not the Keycloak UR
Some typical deployments :
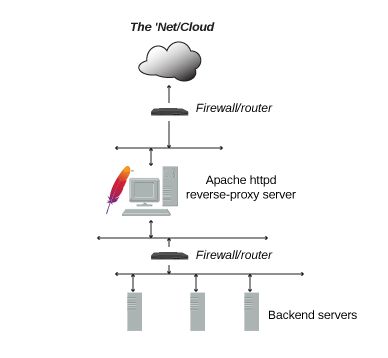
2) Architectural deployment example
A typical reverse proxy architecture can consist of the following elements:
- 2 firewalls
- DMZ
- Reverse proxy
- Keycloak server
- private LAN
2.1) Role of the DMZ
It is a physical or logical subnetwork that contains and exposes an organization’s external-facing services to an untrusted network, usually a larger network such as the Internet. The purpose of a DMZ is to add an additional layer of security to an organization’s local area network (LAN): an external network node can access only what is exposed in the DMZ, while the rest of the organization’s network is firewalled. The DMZ functions as a small, isolated network positioned between the Internet and the private network and, if its design is effective, allows the organization extra time to detect and address breaches before they would further penetrate into the internal networks.
2.2) First firewall (internet – DMZ)
- It sits between the internet and the DMZ
2.3) Second Firewall
- it sits between the DMZ and a local LAN
2.4) Reverse Proxy – DMZ
- It is located in the DMZ
- It has access to the internet an forwards the requests to the keycloak Authentication server which is located on a private LAN
2.5) Keycloak authentication Server – LAN
- It is located on a private network LAN
| With such an architecture: Direct access to keycloak console should never be possible from the external it is not only possible to connect to the keycloak admin console locally (i.e from the private LAN) |
Such an architecture prevents external intruders to get access to the keycloak admin console to access sensitive information (secret …)
3) HTTPS everywhere
Any outgoing or incoming traffic either to the web server reverse proxy or keycloak server should be encrypted with https
4) Reverse Proxy server used with Keycloak
-
2 reverse Proxy engines are available with Keycloak:
- Apache2
-
NGINX
- New Keycloak online training - 19 janvier 2022
- Sizing Keycloak or Redhat SSO projects - 8 juin 2021
- Keycloak.X Distribution - 28 janvier 2021