Using Impersonation with Keycloak : Impersonation is very useful feature in IAM system today. It allows to execute an action being logged as dedicated admin-user to act on specific user actions, as if it was the genuine user who was performing the action. We will learn in this article what it’s intended for and how to implement it within keycloak.
1) Presentation
A typical use case is help desk with people asking the help desk to reset their password, when they have forgotten it.
The keycloak admin, which act as kind of « super-admin » can manage all realms and users, and can perform impersonation. But it would be very really cumbersome to give help desk users access the keycloak admin console !
Hence keycloak offers the ability to define users which can perform impersonation either :
- From master level (global level)
- or from the realm itself
Those users will have impersonate roles assigned to them
2) Defining a local realm admin with impersonate privileges
At first, let’s create a local admin in realm demo (called
admin-user).
To this user is assigned
realm-management client role
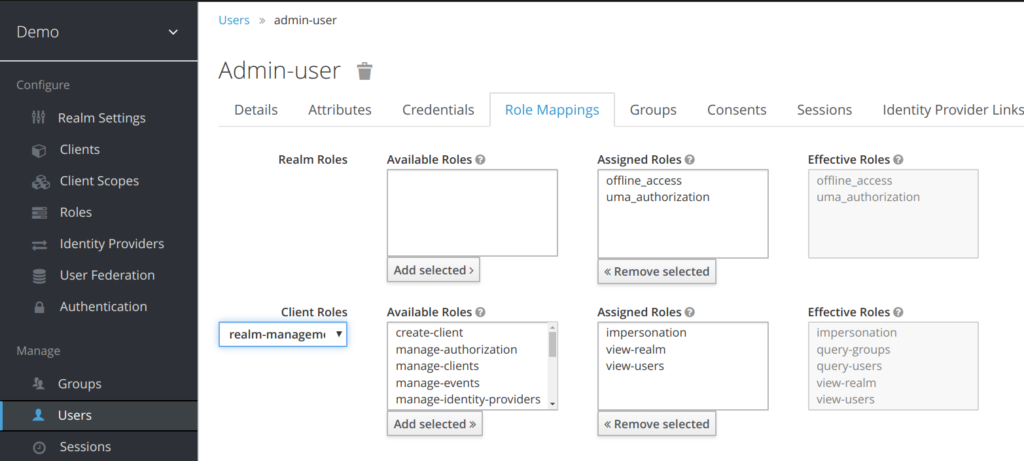
The goal is this local realm admin to be able to perform impersonation.
The roles assigned to admin-user are :
- impersonation
- view-realm
- view-users
The last 2 roles allows the local admin-user to access to realm panel and view the user.
3) Impersonation in action
Each realm has a dedicated Admin Console that can be accessed by
going to the url /auth/admin/{realm-name}/console.
In our case:
- goto https://localhost:8080/auth/admin/demo/console
- enter admin-user as username
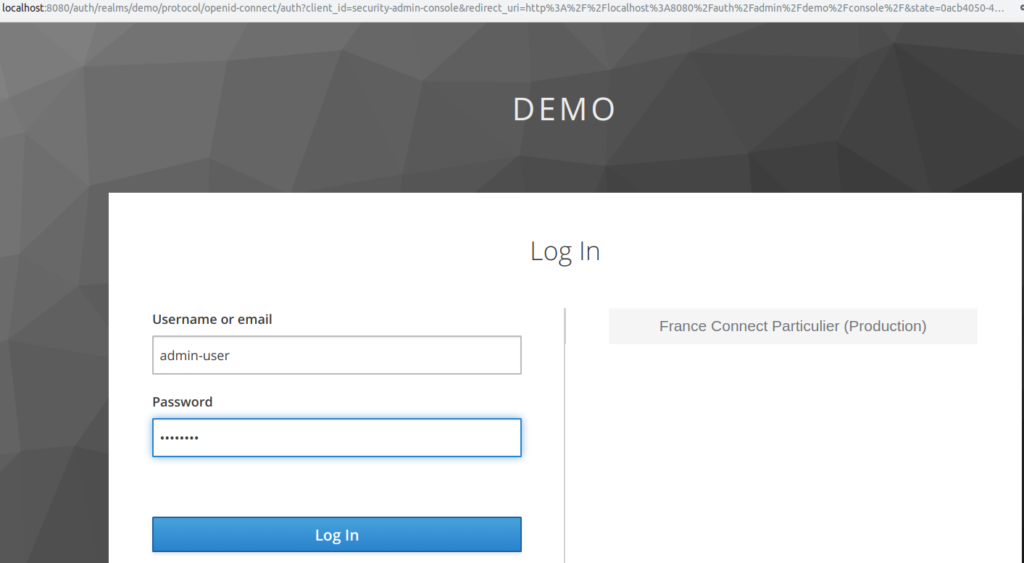
Once the local admin-user is logged, he can access to the realm and list all the users in realm.
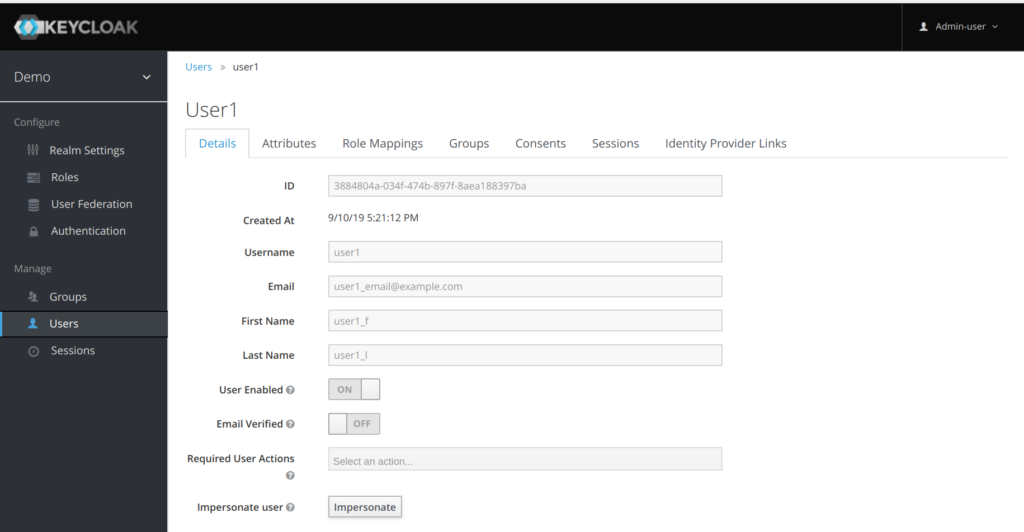
Thus he is able to zoom on a specific user like user1, and also impersonate it when clicking on teh impersonate button.
4) Pointers
- New Keycloak online training - 19 janvier 2022
- Sizing Keycloak or Redhat SSO projects - 8 juin 2021
- Keycloak.X Distribution - 28 janvier 2021